3.2. Borda count election¶
This example of a Borda count election is found in the Borda folder. In the IBorda.sol file, you will find a description of the system and the interface that should be implemented by the contracts.
Read Borda.sol and Borda.spec to understand the system and the properties. You might encounter new features of CVL which later lessons address. The goal in this lesson is to practice understanding violations.
Tip
The bugs are relatively simple and can easily be found manually. Avoid looking for bugs manually before running the Prover. Instead, follow the Prover’s counterexamples to locate the bugs. Counterexamples may vary from one run to the other, we provide links and hints to a run which may differ from your own run.
Look at the following links (or run the provided conf files) of four faulty implementations and understand the violation.
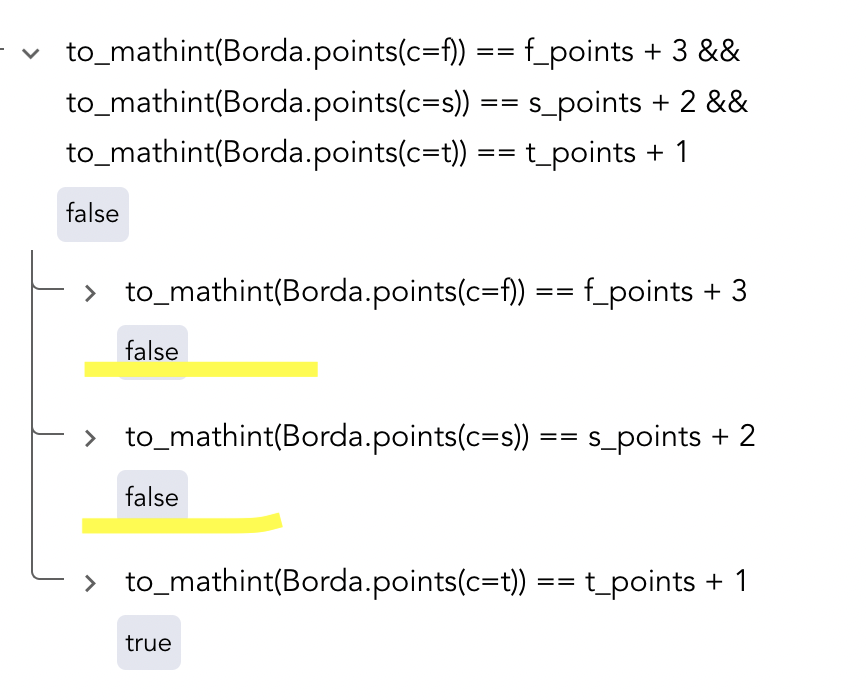
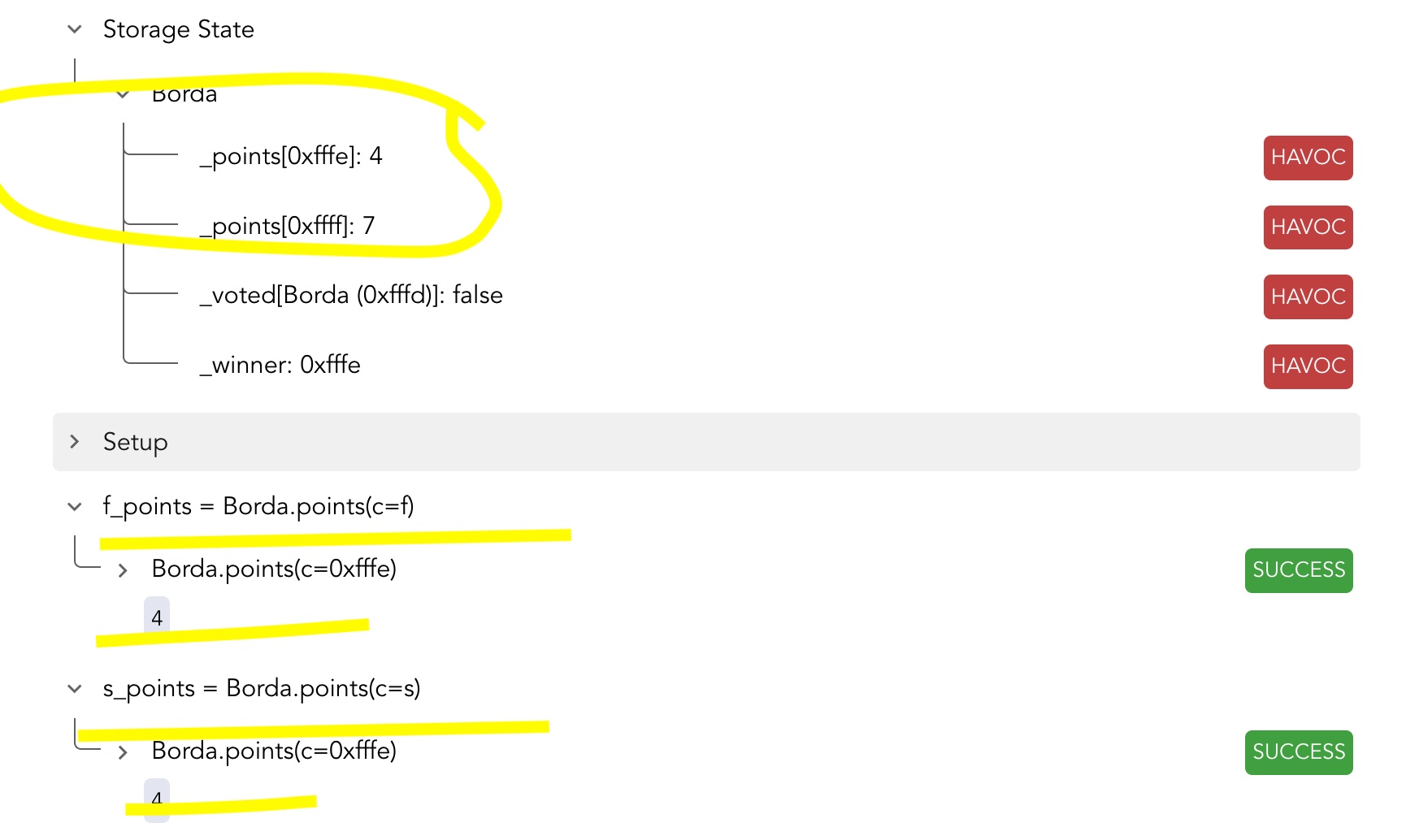
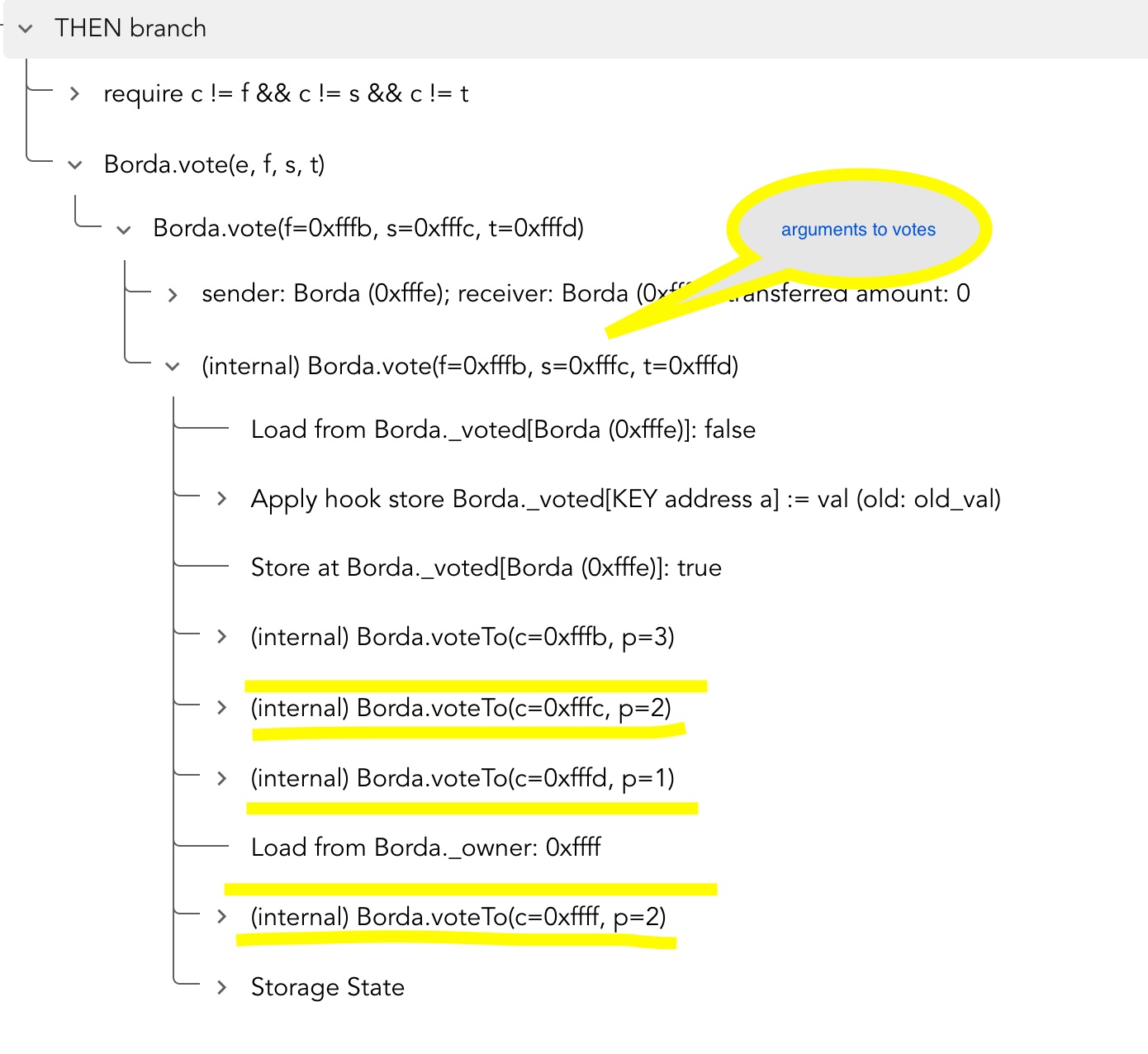
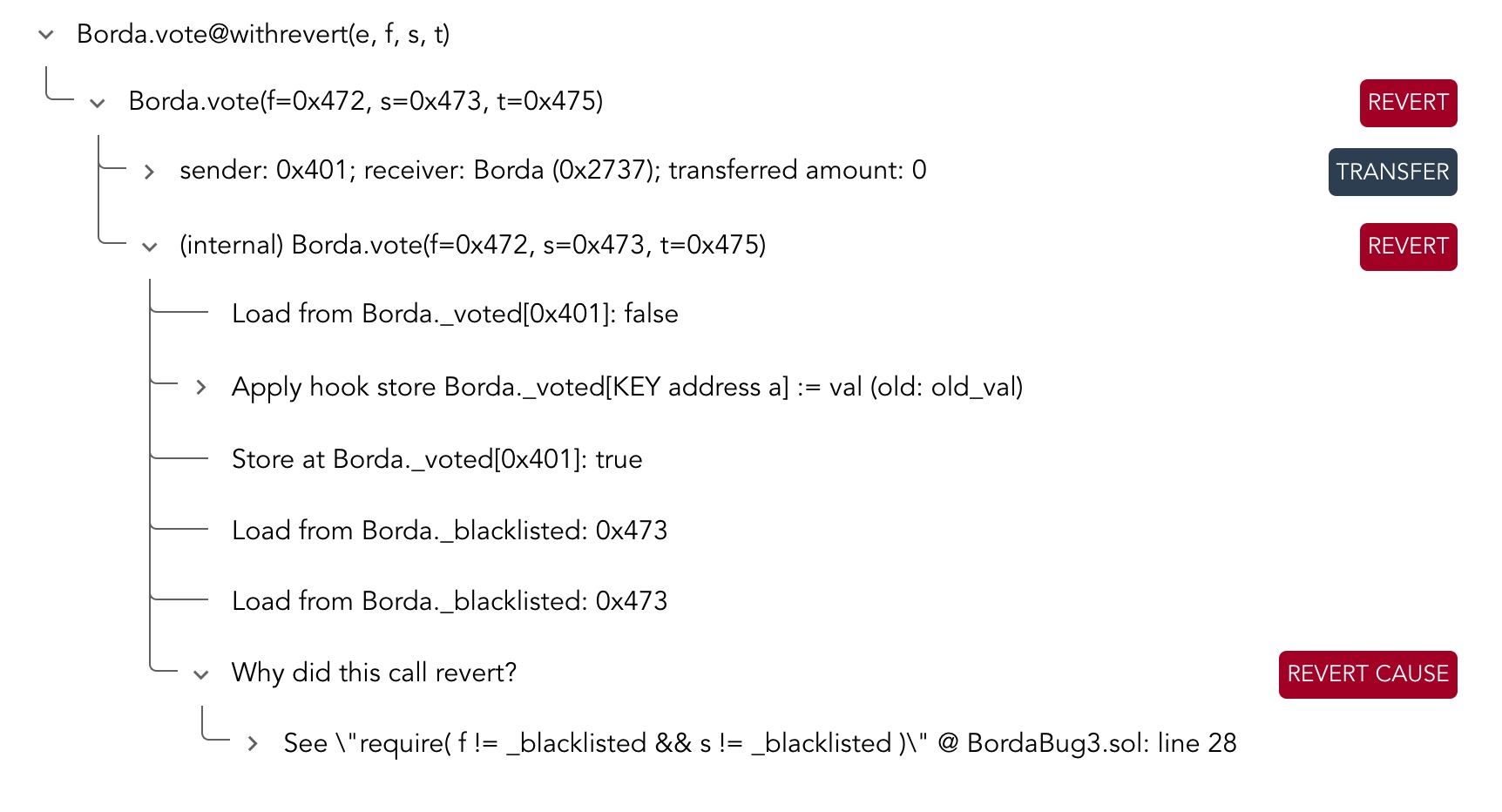
Results of verification Borda Bug1 Report , run with BordaBug1.conf
Results of verification Borda Bug2 Report , run with BordaBug2.conf
Results of verification Borda Bug3 Report , run with BordaBug3.conf
Results of verification Borda Bug4 Report , run with BordaBug4.conf
Tip
Use the file tree view (third icon on the left panel) to view the files in this verification run to check your conclusions.
Hints for Borda¶
The best way to understand the coverage of the spec is via bug injection. Our CertoraMutate and Gambit tools help performing this task. According to the Borda mutation report the coverage is 100%, which means that all mutants were caught by at least one rule. However, the type of mutants Gambit generates is limited and there might be an injected bug that will point at a missing rule.